HHS IT Security Program “Not Effective,” Says OIG FISMA Audit
HHS OIG has determined that the department’s IT security program was “not effective” because it did not meet security levels required by the Federal Information Security Modernization Act.

Source: HHS
- HHS OIG has determined that the department’s IT security program was “not effective” because it did not meet security levels required by the Federal Information Security Modernization Act (FISMA).
OIG identified HHS IT security weaknesses in the areas of risk management, configuration management, identity and access management, data protection and privacy, security training, IT security continuous monitoring, incident response, and contingency planning.
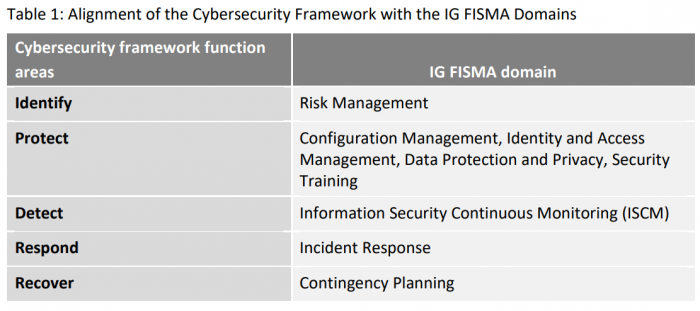
In the report, OIG mapped the FISMA domains to the NIST Cybersecurity Framework functional areas (see Table 1).
HHS received a level 2 (defined) score in the NIST Cybersecurity Framework areas of detect, respond, and recover. A level 2 score means that “policies, procedures, and strategies are formalized and documented but not consistently implemented.”
The department received a level 3 (consistently implemented) score in the NIST areas of identify and protect. A level 3 score indicates that “policies, procedures, and strategies are consistently implemented, but quantitative and qualitative effectiveness measures are lacking.”
Within the context of the NIST maturity model, level 4 (managed and measurable) represents an effective level of security, explained OIG. A level 4 score indicates that "quantitative and qualitative measures on the effectiveness of policies, procedures, and strategies are collected across the organization and used to assess them and make necessary changes." HHS failed to receive a level 4 score in any of the NIST functional areas.
Source: HHS OIG
HHS Working with DHS to Implement CDM Program
To improve information security, HHS is working with the Department of Homeland Security (DHS) to implement a continuous diagnostics and mitigation (CDM) program.
CDM is a dynamic approach to strengthening the cybersecurity of government networks and systems. The CDM Program provides federal agencies with capabilities and tools to "identify cybersecurity risks on an ongoing basis, prioritize these risks based on potential impacts, and enable cybersecurity personnel to mitigate the most significant problems first. Congress established the CDM program to provide adequate, risk-based, and cost-effective cybersecurity and more efficiently allocate cybersecurity resources," DHS explained on its website.
For CDM, sensors perform an automated search for cybersecurity vulnerabilities. Results from the sensors feed into a dashboard that produces customized reports alerting network managers to the most critical cyber risks.
Prioritized alerts enable agencies to allocate resources based on the severity of the risk. Progress reports track results, which can be used to compare security postures among agency networks. Summary information feeds into a federal enterprise-level dashboard to provide situational awareness into cybersecurity risk posture across the federal government.
For HHS, the CDM program includes continuous monitoring of its networks and systems, documenting its operating divisions’ (OPDIVs) progress in addressing and implementing cybersecurity strategies, and reporting progress through DHS dashboards.
“HHS needs to ensure that all OPDIVs consistently review and remediate or address the risk presented by vulnerabilities discovered, consistently implement account management procedures, and accurately track systems to ensure they are operating with a current and valid Authority to Operate,” the audit noted.
“Additionally, the Department should focus on configuring recently deployed continuous diagnostic monitoring tools to automate the integration of cyber risks into newly developed enterprise risk management programs. These steps will strengthen the program and further enhance the HHS mission,” it added.
The original version of FISMA was included in Title III of the E-Government Act of 2002, which required each federal agency to develop, document, and implement an agency-wide program to provide information security for the information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other sources.
In 2014, Congress passed amendments to FISMA designed to reduce the amount of overall reporting, strengthen the use of continuous monitoring in systems, increase the focus on agencies for compliance, and increase reporting that is more focused on the issues caused by security incidents.
"The ultimate objective is to conduct the day-to-day operations of the agency and to accomplish the agency's stated missions with adequate security, or security commensurate with risk, including the magnitude of harm resulting from the unauthorized access, use, disclosure, disruption, modification, or destruction of information," explained NIST on its website.
